The Tor Browser: A Comprehensive Guide
The Tor Browser: A Comprehensive Guide
The Tor Browser is a free and open-source web browser that allows users to browse the internet anonymously. It was developed by the Tor Project, a non-profit organization that works to protect online privacy and freedom of expression.
The browser works by routing traffic through a series of volunteer-run servers around the world. This process, called onion routing, encrypts traffic multiple times and makes it very difficult to track its origin or destination.
The browser is used by a wide range of people, including journalists, activists, human rights workers, and people who simply want to protect their privacy online. It is also used by people who live in countries with repressive governments, where internet censorship is common.
Why use the Tor Browser?
There are many reasons to use the Tor Browser. Here are a few of the most important:
- Privacy: The browser can help to protect your privacy online by making it difficult for websites and other third-party trackers to track your activity.
- Security: The browser can also help to protect you from security threats, such as malware and phishing attacks.
- Freedom of expression: The browser allows you to browse the internet freely without fear of censorship or reprisal.
How does the Tor Browser work?
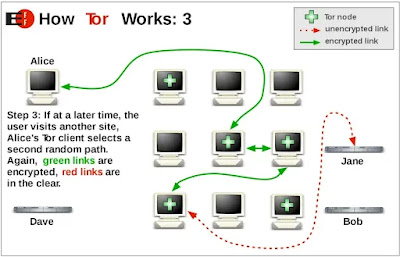
When you connect to a website using the Tor Browser, your traffic is first encrypted and then routed through a series of three relays. The first relay is called the entry guard, the second relay is called the middle relay, and the third relay is called the exit relay.
Each relay decrypts one layer of encryption from the traffic and then forwards it to the next relay in the chain. The exit relay is the only relay that knows the destination of the traffic. The entry guard and middle relays only know the relay that came before and the relay that came after.
This process of routing traffic through multiple relays makes it very difficult for anyone to track your online activity. Even if an attacker were able to compromise one of the relays, they would only be able to see the IP address of the relay that came before and the relay that came after. They would not be able to see your IP address or the IP address of the website you are visiting.
How to use the Tor Browser
To use the Tor Browser, simply download and install it from the Tor website. Once you have installed the browser, you can start using it to browse the internet anonymously.
Simply open the browser and start browsing as usual. The browser will route your traffic through the Tor network, which will conceal your location and online activity from anyone conducting network surveillance or traffic analysis.
Tips for using the Tor Browser
Here are a few tips for using the Tor Browser:
- Keep your browser up to date: The browser is updated regularly with new security features and bug fixes. It is important to keep your browser up to date to ensure that you are protected from the latest threats.
- Use a strong password: It is important to use a strong password for your Tor Browser account. This will help to protect your account from unauthorized access.
- Be careful about what links you click on: The browser can help to protect you from phishing attacks, but it is important to be careful about what links you click on. If you receive an email or message with a link, do not click on it unless you are sure that it is from a trusted source.
- Use HTTPS whenever possible: HTTPS is a secure protocol that encrypts traffic between your browser and the website you are visiting. It is important to use HTTPS whenever possible to protect your traffic from eavesdropping.
Limitations of the Tor Browser
The Tor Browser is a powerful tool for protecting your privacy and security online, but it is important to be aware of its limitations.
- Speed: The browser can be slower than other web browsers because it has to route traffic through multiple relays.
- Compatibility: The browser is not compatible with all websites and online services. Some websites and online services block Tor traffic.
- Fingerprinting: It is possible to fingerprint Tor users based on their browsing behavior. However, there are steps that Tor users can take to reduce the risk of fingerprinting.
Conclusion
The Tor Browser is a powerful tool for protecting your privacy and security online. It is used by a wide range of people, including journalists, activists, human rights workers, and people who simply want to protect their privacy online.
If you are concerned about your privacy and security online, I encourage you to download and use the Tor Browser.





Comments